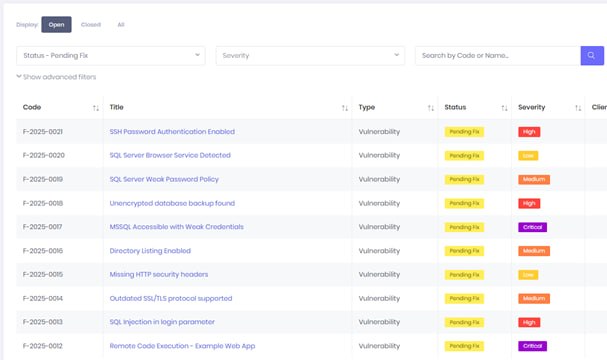
Our Credentials
Industry Certified Experts
Every engagement is led by professionals with hands-on offensive security experience.

OSCP
Offensive Security Certified Professional
CISSP
Certified Information Systems Security Professional

CRTO
Certified Red Team Operator

PNPT
Practical Network Penetration Tester
Our testers think like attackers because they are trained as attackers. These are not checkbox certifications - they require hands-on exploitation of real systems under exam conditions. When we test your business, we use the same techniques and tools that real threat actors use, applied with the discipline and methodology of experienced professionals.